About a year ago now, we learned that the APIBAN project published a new APIBAN client that uses fail2ban. I did a write-up at the time, but a year onwards, with FPBX 17 in full swing, it’s time to recap for this week’s #FridayFun.
If you’re a PBX administrator and are not already aware of APIBAN, you want to run (not walk) over to their website at:
APIBAN is a free service that maintains a list of IPs of known bad actors with a focus on telephony. There are published APIs which you can use to develop your own security integrations, and notably for our purposes today, published clients that allow an administrator to secure their systems with minimal effort. The goal with this post is setup the APIBAN fail2ban client on a FBPX 17 system. This client is not recommended with earlier distro versions, as the fail2ban version is too old for efficient integration.
The fail2ban client lives on GitHub. If you’re the type that likes to peek under the covers, you can see the code and docs here:
Installation steps:
- Starting with a FPBX 17 system with the FPBX Firewall module configured and working.
- Disable fail2ban email notifications if it’s enabled. There will be a LOT of bans; you do not want email notifications for each!
- Things look much cleaner in the GUI if you enable the Firewall module option, Intrusion Detection Sync Firewall. This will be enabled by default on a new install, but if you’ve upgraded from an old version, you will want to browse to Connectivity → Firewall → Advanced (from flyout menu) → Advanced Settings and set Intrusion Detection Sync Firewall to Enable.
- Increase the fail2ban ban time to at least 7 days, the APIBAN client does a full refresh weekly, and just incremental updates in between. You don’t want bans to expire before the flush happens. I’m using a value of 610000 seconds, just over 7 days.
- Get a free APIBAN key from https://apiban.org. If you already have a key that’s not being used, you might find it in the file
/usr/local/bin/apiban/config.jsonbut you can also recover an old key using this page.
To install run the one line command, remembering to substitute your actual key in place of APIBANKEY:
curl -sSL https://raw.githubusercontent.com/apiban/apiban-fail2ban/main/install.sh | bash -s -- APIBANKEY
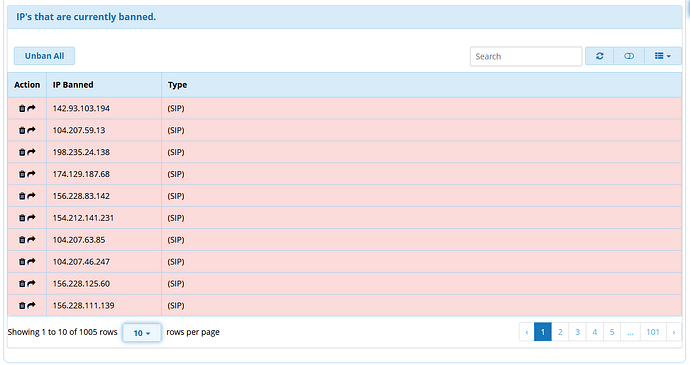
I’m testing using a low spec VM from vultr, so it took several minutes for the install to complete. While waiting, you can monitor the progress of the initial sync in the GUI by browsing to the Intrusion Detection tab in the Firewall module. You will see the Ban list slowly grow as the entries are synced.
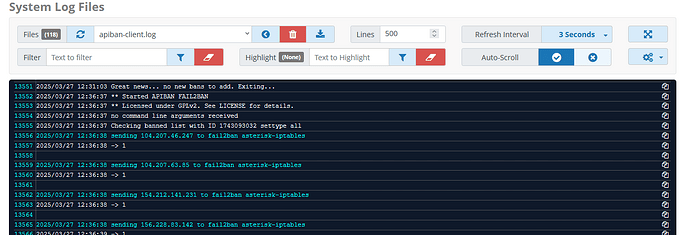
After a few minutes you’ll see the client install finish. A periodic check of the ban list will show the numbers fluctuate from time to time so you know something is happening, but perhaps you’d like to know what. By default, the APIBAN client logs to the file /var/log/apiban-client.log. If you’re comfortable with the command line, you can grep away there. If you want to browse the logs using the GUI, there’s one more step. Run this command:
ln -s /var/log/apiban-client.log /var/log/asterisk/apiban-client.log
This will create a symlink to the APIBAN log in /var/log/asterisk/. Now you can use Reports → System Logfiles to see the logged APIBAN events by selecting apiban-client.log from the dropdown menu:
So if you find yourself sleeping a little easier at night, send some positive energy to @fredposner and the other fine folks at APIBAN for providing this service!