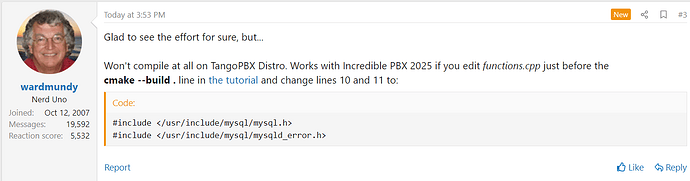
[Below, replace * with Free, Tango, or Incredible]
Questions that come to mind about a sysadmin module… beginning with a comment… thank you for taking on this effort. I am 100% behind any open-source *PBX module development.
That said, I would back up and ask the question “why sysadmin?” For GUI-based administration of all things Linux, including the network stack, web server, email server, vpn server, etc., there are existing tools. Webmin and Cockpit are two that come to mind. I guess what I am thinking about is separation of concerns. Other than single-screen convenience, what is the big value (considering risk, see below) a sysadmin PBX module brings.
Why shouldn’t the management of the network have to be done by the root user – which is not to say, someone who can access the *PBX admin GUI, but actual root. In a lot of cases, PBX admin and root user are one and the same. Yet we pretend that we have separation of user and root by chowning everything as asterisk and running the daemons as asterisk and still logging in and working as root all the time…
What I am getting at is perhaps root-level admin stuff should be completely separated from *PBX. For something like firewall, which actually does make a lot of sense to control from the PBX GUI, write a server daemon that runs as root to alter nftables and has a tight API that the PBX can interact with. I recognize that firewall is not in scope here with your module. In FreePBX (commercial), sysadmin and firewall are tightly coupled, and this is problematic.
Take note that a vulnerabilty in a Sangoma commercial module a few years ago resulted in attackers being able to pop stuff in incron and run as root. I know you’re not using incron here, but the point is, this (sysadmin, system-root-level interaction) is going to be the area where black hats focus their attention.
Having already made my case against “The Sangoma way” I will say that the other two ways have a couple issues in my opinion. Sudo is going to require manual setup to start with. Setuid binary requires the php script to make a system call to it and system/shell calls are a common place for hackers to bust through. The fourth way I previously mentioned, a strictly controlled server daemon with a tight API to talk to it, is probably the most secure.